I am an applied scientist at Amazon Web Services, working on Agentic AI for security. I earned my Ph.D. in the Department of Electrical and Computer Engineering at The University of Texas at Austin, supervised by Prof. Mohit Tiwari. I also worked closely with Prof. Sarfraz Khurshid. My research interests mainly lie in software security, automated reasoning, machine learning, and software engineering. Before UT Austin, I worked with Prof. Abhik Roychoudhury at NUS, and Prof. John C.S. Lui at CUHK. I received my bachelor’s and master’s degrees with honors from Xi’an Jiaotong University.
Fixing Privilege Escalations in Cloud Access Control with MaxSAT and Graph Neural Networks
ASE 2023
SymMC: Approximate Model Enumeration and Counting Using Symmetry Information for Alloy Specifications
ESEC/FSE 2022
SapientML: Synthesizing Machine Learning Pipelines by Learning from Human-Written Solutions
ICSE 2022 • work done during internship at Fujitsu Research of America - AI Lab
ACHyb: A Hybrid Analysis Approach to Detect Kernel Access Control Vulnerabilities


ESEC/FSE 2021
Exploiting Non-Uniform Program Execution Time to Evade Record/Replay Forensic Analysis
Computers & Security (Elsevier), Apr 2019
Taming Energy Cost of Disk Encryption Software on Data-Intensive Mobile Devices
Future Generation Computer Systems (Elsevier), Sep 2017
Adjusting satisfiability modulo theories solver configurations
US-12517809-B1 • Amazon Technologies, Inc. • Published Jan 6, 2026
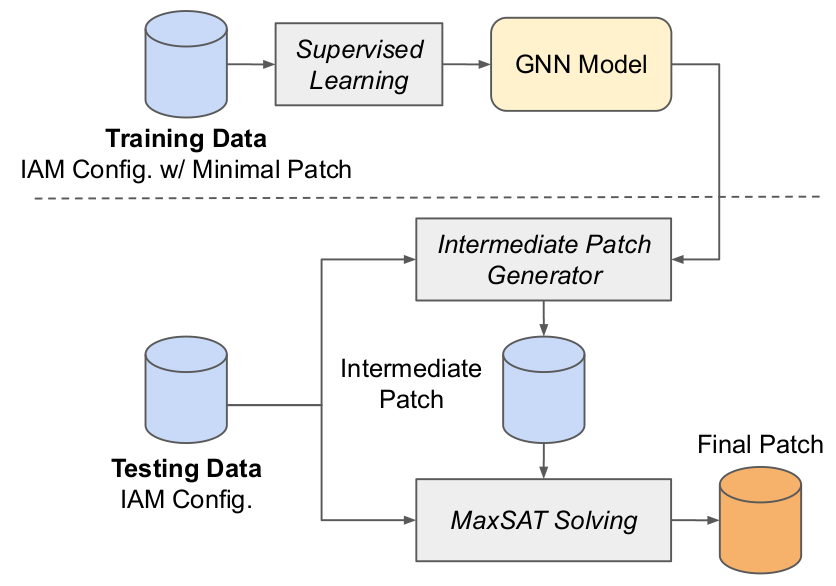
Addressing privilege escalations in cloud access control configurations is crucial for improving security assurance. We propose an IAM Privilege Escalation Repair Engine (IAMPERE) that utilizes MaxSAT and Graph Neural Networks to efficiently generate an approximately minimal patch for repairing a broader range of privilege escalations.
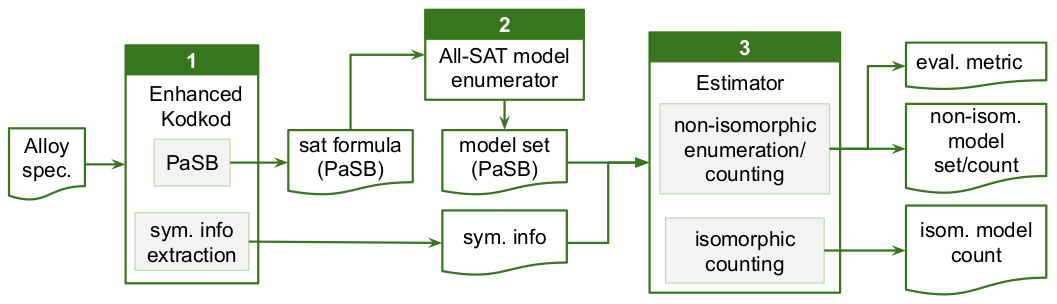
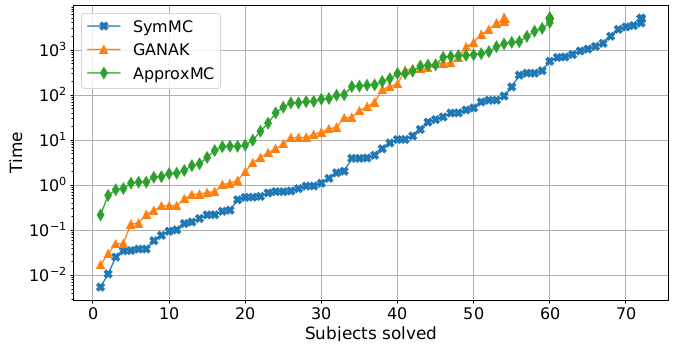
Alloy provides first-order relational logic for writing specs with an automatic backend for analysis. We present SymMC, which leverages symmetry information to improve the efficiency of model enumeration and counting for Alloy specifications.
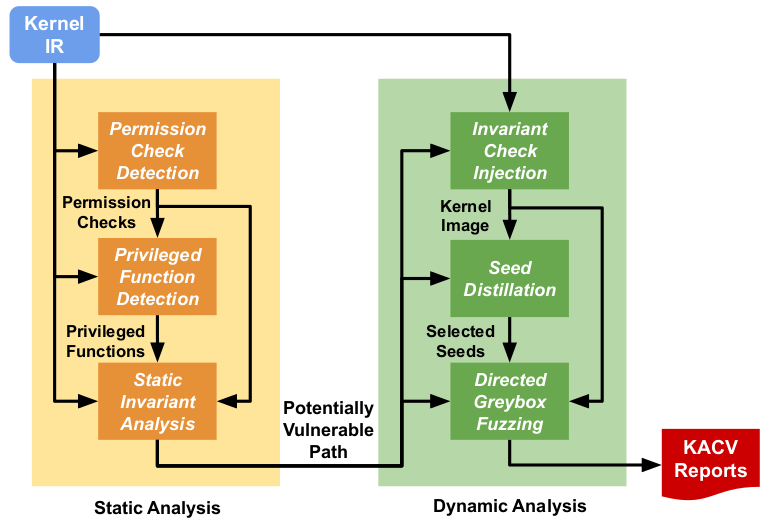
Incorrect access control implementation can introduce Kernel Access Control Vulnerabilities (KACVs). We propose ACHyb, a precise and scalable hybrid analysis approach to detect KACVs due to missing or misused permission checks.
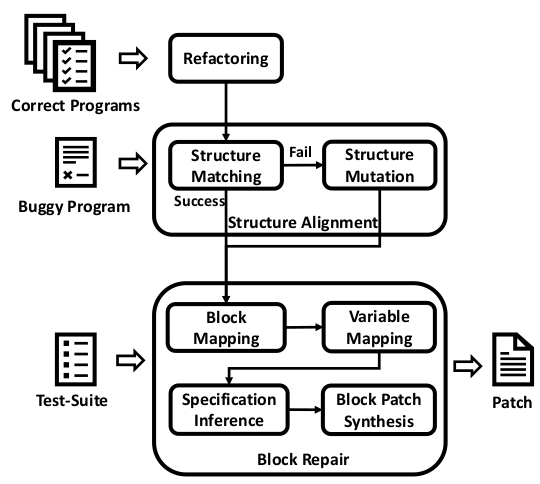
We repair severely incorrect programs given at least one reference solution by refactoring reference programs to generate diverse correct variants, enabling block-level patch synthesis. This has been applied to intelligent tutoring for programming education.